Analyzing Privacy Violations - Part 1: "Types of Privacy Violations and Their Impact"
Today’s lesson delves into the critical examination of privacy violations, their real-world impacts, and the actors behind these breaches. By understanding the mechanisms of privacy infringements and identifying those responsible, you will gain deeper insight into safeguarding personal and organizational data.
“Types of Privacy Violations and Their Impact”
Explore real-world examples of privacy violations and their consequences on individuals and society, providing valuable context for the risks posed by inadequate privacy protections.
1. Views of data privacy risks, personal data and digital privacy laws
Online privacy is complex, encompassing debates over law enforcement’s data access, government regulation and what information companies can collect. This chapter examines Americans’ perspectives on these issues and highlights how views vary across different groups, particularly by education and age.
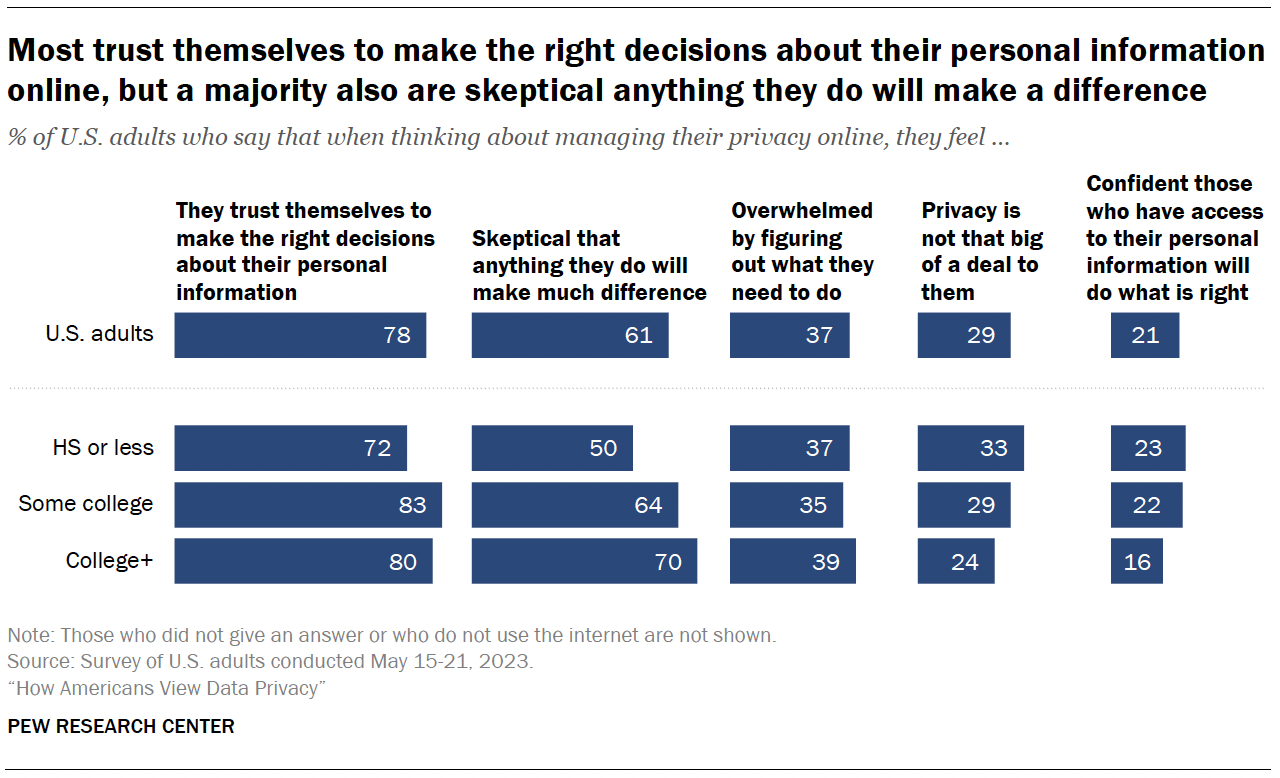
When managing their privacy online, most Americans say they trust themselves to make the right decisions about their personal information (78%), and a majority are skeptical that anything they do will make a difference (61%).
Far fewer mention being overwhelmed by figuring out what they need to do (37%) or say privacy is not that big of a deal to them (29%).
Another 21% are confident that those with access to their personal information will do what is right.
Education differences
- 81% of those with at least some college experience say they trust themselves to make the right decisions about their personal information online, compared with 72% of those with a high school diploma or less.
- 67% of those with at least some college are skeptical that anything they do to manage their online privacy will make a difference, compared with half of those with a high school diploma or less formal education.
On the other hand, those with a high school education or less are more likely than those with some college experience or more to say that privacy isn’t that big of a deal to them and that they are confident that those who have access to their personal information will do the right thing.
Personal data and information
The survey also explores the concerns people have about data collection and security – specifically, how they feel about three scenarios around companies, law enforcement and identity theft.
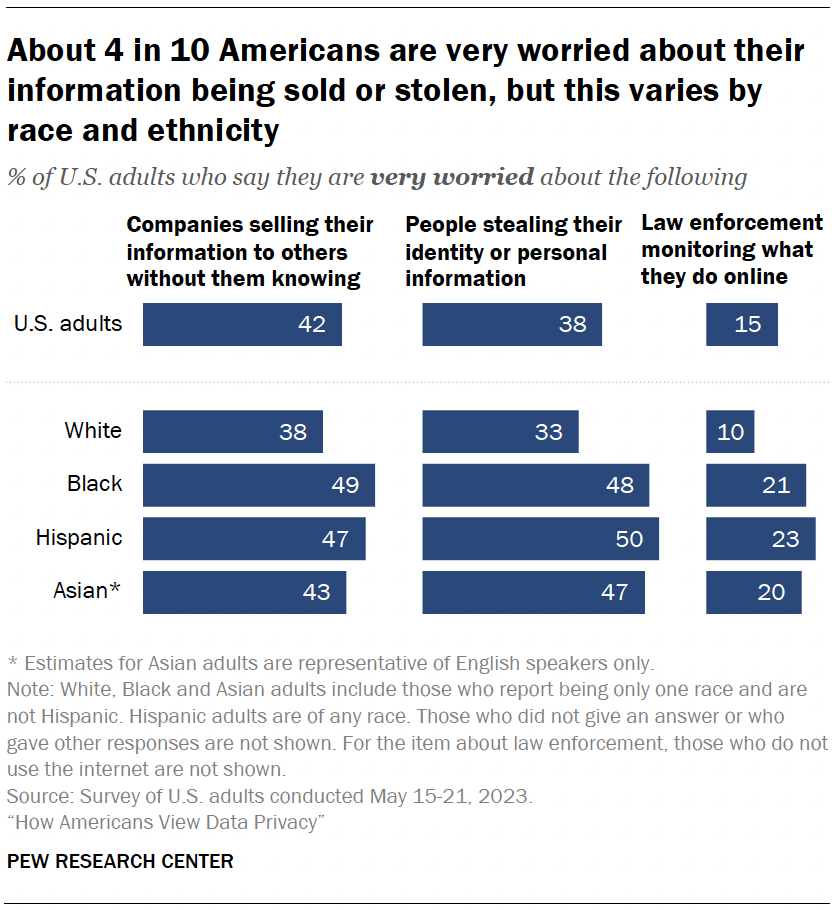
Roughly four-in-ten Americans say they are very worried about companies selling their information to others without them knowing (42%) or people stealing their identity or personal information (38%). Fewer are apprehensive about law enforcement monitoring what they do online (15%).
Racial and ethnic differences
However, some of these shares are higher among Hispanic, Black or Asian adults:1
- Roughly half of Hispanic, Black or Asian adults are very worried about people stealing their identity or personal information, compared with a third of White adults.
- About one-in-five of each group are very worried about law enforcement monitoring their online activity; 10% of White adults say this.
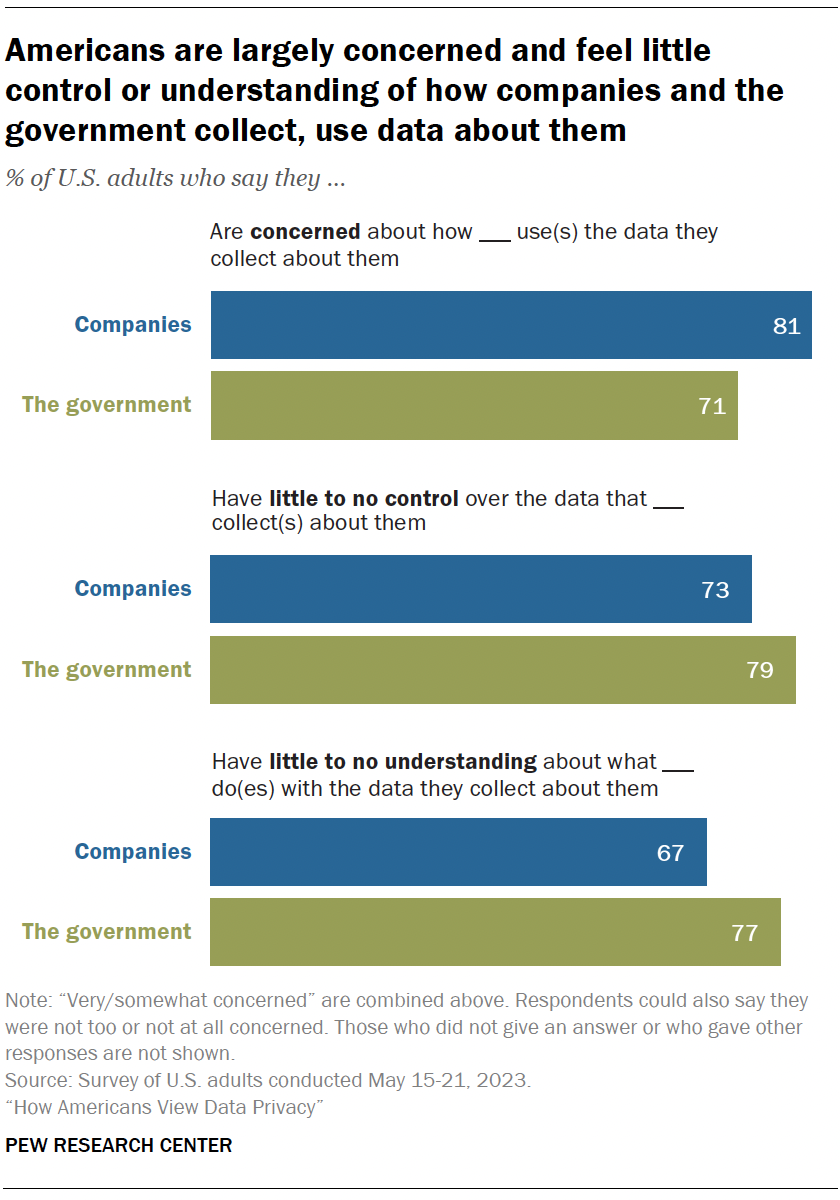
Feelings of concern, confusion and a lack of control over one’s data
A majority of Americans say they are concerned, lack control and have a limited understanding about how the data collected about them is used. This is true whether it’s the government or companies using their data. Similar sentiments were expressed in 2019, when we last asked about this.
Concern is high: 81% say they feel very or somewhat concerned with how companies use the data they collect about them. Fully 71% say the same regarding the government’s use of data.
People don’t feel in control: Roughly three-quarters or more feel they have very little or no control over the data collected about them by companies (73%) or the government (79%).
Understanding is low: Americans also say they don’t understand what these actors are doing with the data collected about them. Majorities say they have very little or no understanding of this, whether by the government (77%) or companies (67%).
Americans are now less knowledgeable than before about how companies are using their personal data. The share who say they don’t understand this has risen from 59% in 2019 to 67% in 2023.
They have also grown more concerned about how the government uses the data it collects about them, with the share expressing concern up from 64% to 71% over this same period.
While these sentiments have not changed significantly since 2019 among Democrats and those who lean toward the Democratic Party, Republicans and GOP leaners have grown more wary of government data collection. Today, 77% of Republicans say they are concerned about how the government uses data it collects about them, up from 63% four years earlier.
Privacy laws and regulation
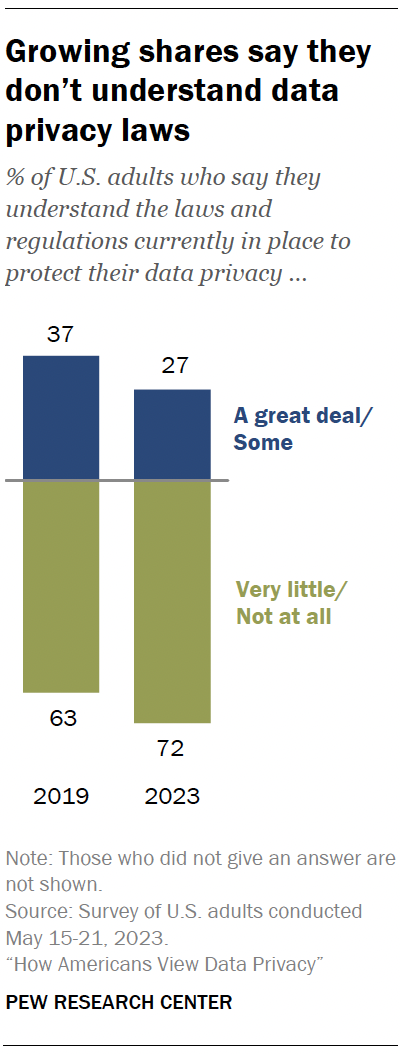
Americans are less knowledgeable about data privacy laws today than in the past.
Today, 72% of Americans say they have little to no understanding about the laws and regulations that are currently in place to protect their data privacy. This is up from 63% in 2019.
By comparison, the shares who say they understand some or a great deal about these laws decreased from 37% in 2019 to 27% in 2023.
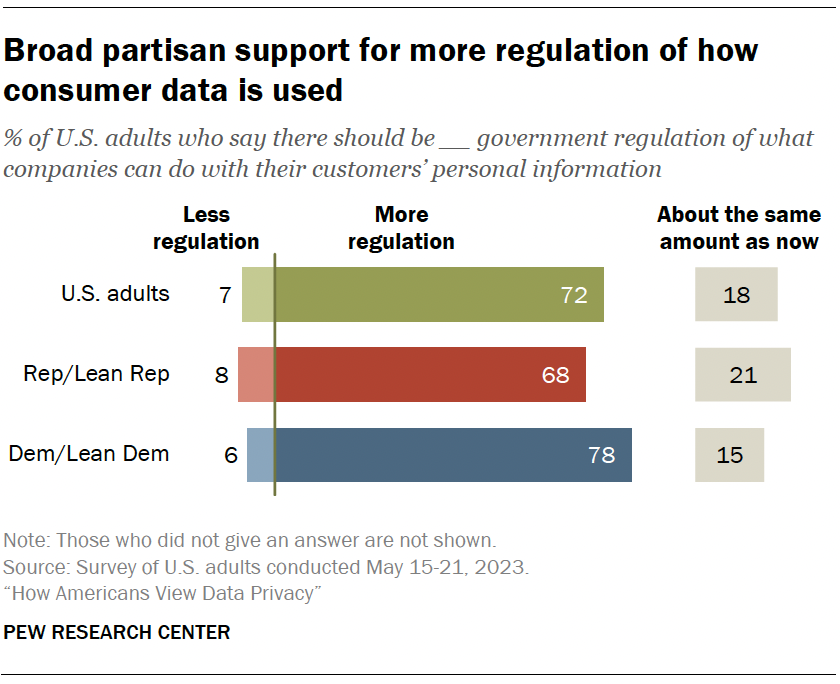
Americans largely favor more regulation to protect personal information
Overall, 72% say there should be more government regulation of what companies can do with their customers’ personal information. Just 7% say there should be less regulation. Another 18% say it should stay about the same.
Views by political affiliation
There is broad partisan support for greater involvement by the government in regulating consumer data.
A majority of Democrats and Republicans say there should be more government regulation for how companies treat users’ personal information (78% vs. 68%).
These findings are largely on par with a 2019 Center survey that showed strong support for increased regulations across parties.
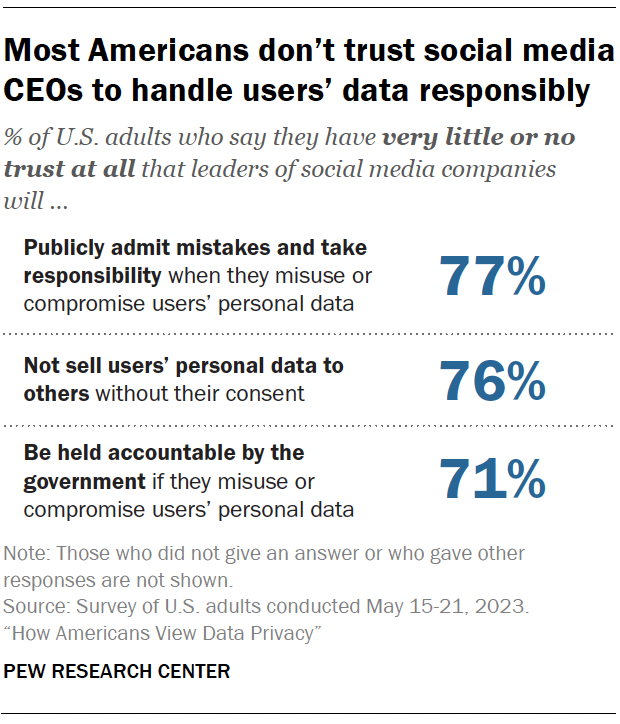
Trust in social media executives
Majorities of Americans say they have little to no trust that leaders of social media companies will publicly admit mistakes regarding consumer data being misused or compromised (77%), that these leaders will not sell users’ personal data to others without their consent (76%), and that leaders would be held accountable by the government if they were to misuse or compromise users’ personal data (71%).
This includes notable shares who have no trust at all in those who are running social media sites. For example, 46% say they have no trust at all in executives of social media companies to not sell users’ data without their consent.
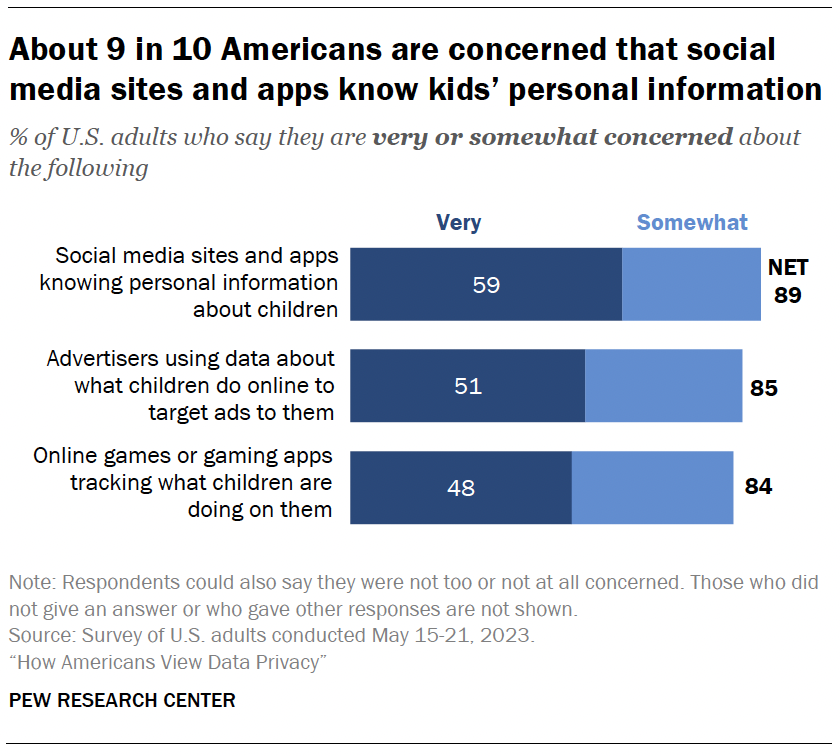
Children’s online privacy: Concerns and responsibility
Most Americans say they are concerned about social media sites knowing personal information about children (89%), advertisers using data about what children do online to target ads to them (85%) and online games tracking what children are doing on them (84%).
Concern is widespread, with no statistically significant differences between those with and without children.
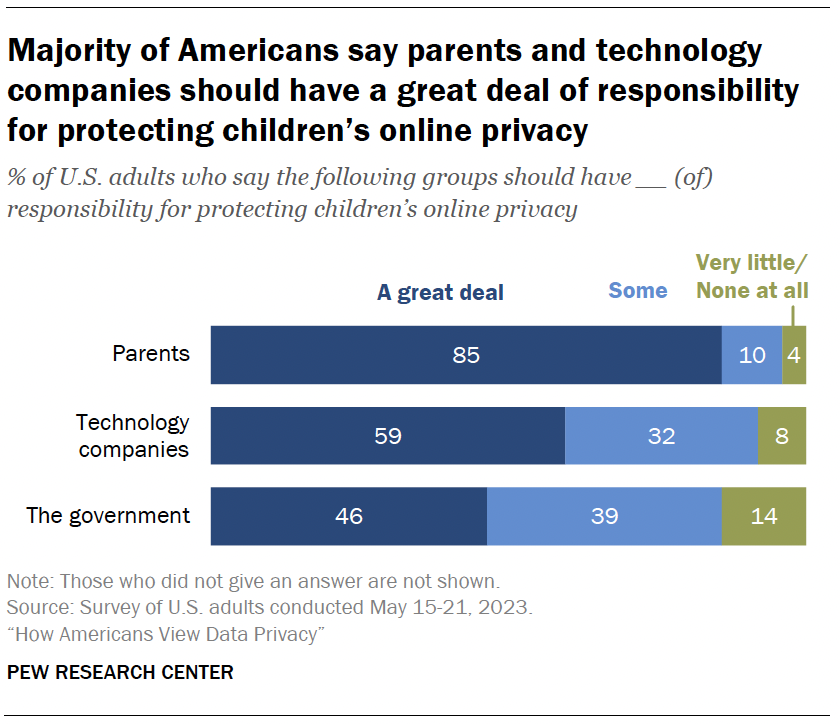
Another key question is who should be responsible for the actual protection of kids’ online privacy.
Fully 85% say parents bear a great deal of responsibility for protecting children’s online privacy. Roughly six-in-ten say the same about technology companies, and an even smaller share believe the government should have a great deal of responsibility.
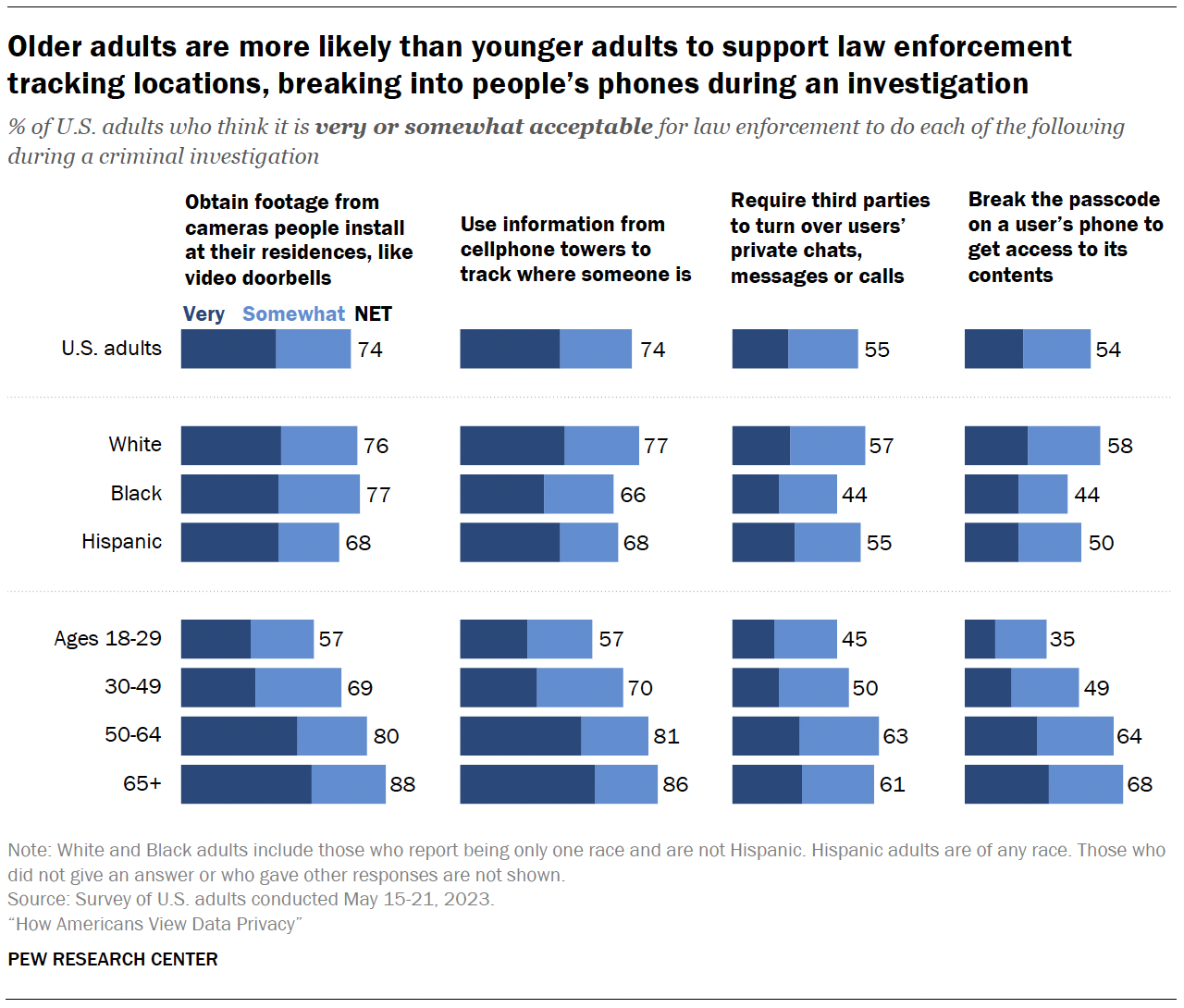
Law enforcement and surveillance
The survey also measured how acceptable Americans think it is for law enforcement to use surveillance tools during criminal investigations.
Roughly three-quarters of Americans say it’s very or somewhat acceptable for law enforcement to obtain footage from cameras people install at their residences during a criminal investigation or use information from cellphone towers to track where someone is.
By comparison, smaller shares – though still a slight majority – say it is acceptable to break the passcode on a user’s phone (54%) or require third parties to turn over users’ private chats, messages or calls (55%) during a criminal investigation.2
About one-in-ten Americans say they aren’t sure how they feel about law enforcement doing each of these things.
Age differences
Older adults are much more likely than younger adults to say it’s at least somewhat acceptable for law enforcement to take each of these actions in criminal investigations.
For example, 88% of those 65 and older say it’s acceptable for law enforcement to obtain footage from cameras people install at their residences, compared with 57% of those ages 18 to 29.
Racial and ethnic differences
In the case of a criminal investigation:
- White adults are more likely than Hispanic and Black adults to think it’s acceptable for law enforcement to use information from cellphone towers to track people’s locations and to break the passcode on a user’s phone to get access to its contents.
- White and Hispanic adults are more likely than Black adults to say it’s acceptable to require third parties to turn over users’ private chats, messages or calls.
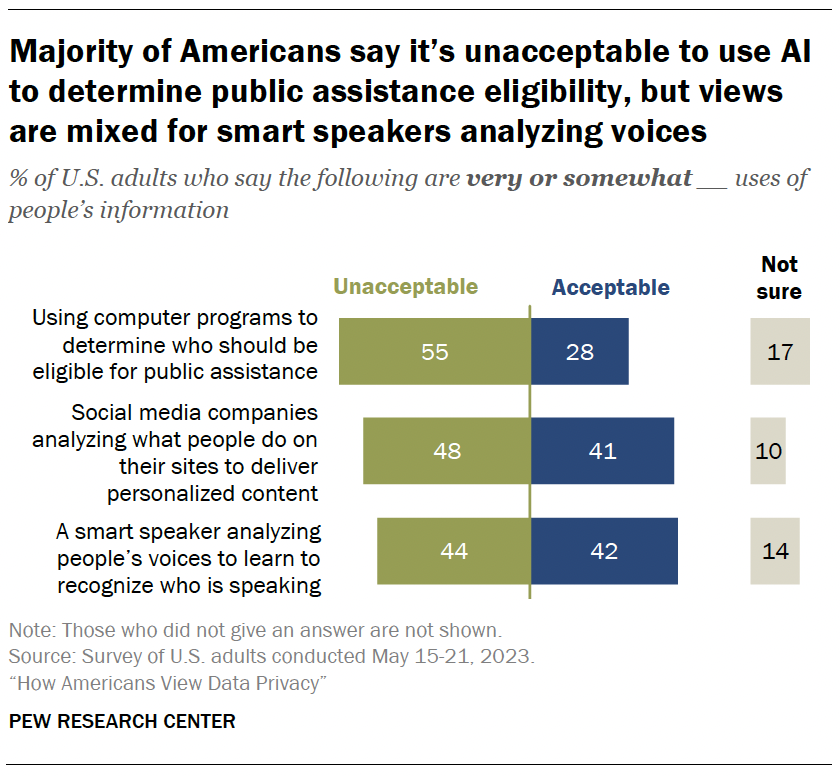
AI and data collection
Artificial intelligence (AI) can be used to collect and analyze people’s personal information. Some Americans are wary of companies using AI in this way.
Fully 55% of adults say using computer programs to determine who should be eligible for public assistance is unacceptable. Roughly a quarter say it’s an acceptable use of AI.
Roughly half (48%) think it is unacceptable for social media companies to analyze what people do on their sites to deliver personalized content. Still, 41% are supportive of this.
Views are mixed when it comes to smart speakers analyzing people’s voices to learn who is speaking. Statistically equal shares say it’s unacceptable and acceptable (44% and 42%, respectively).
And some Americans – ranging from 10% to 17% – are uncertain about whether these uses are acceptable or not.
Age differences
- 49% of adults 50 and older say it’s unacceptable for a smart speaker to analyze people’s voices to learn to recognize who’s speaking. This share drops to four-in-ten among adults under 50.
- Similarly, 56% of those 50 and older say social media companies analyzing what people do on their sites to deliver personalized content is unacceptable. But 41% of those under 50 say the same.
- There are no differences between those under 50 and those 50 and older over whether computer programs should be used to determine eligibility for public assistance.
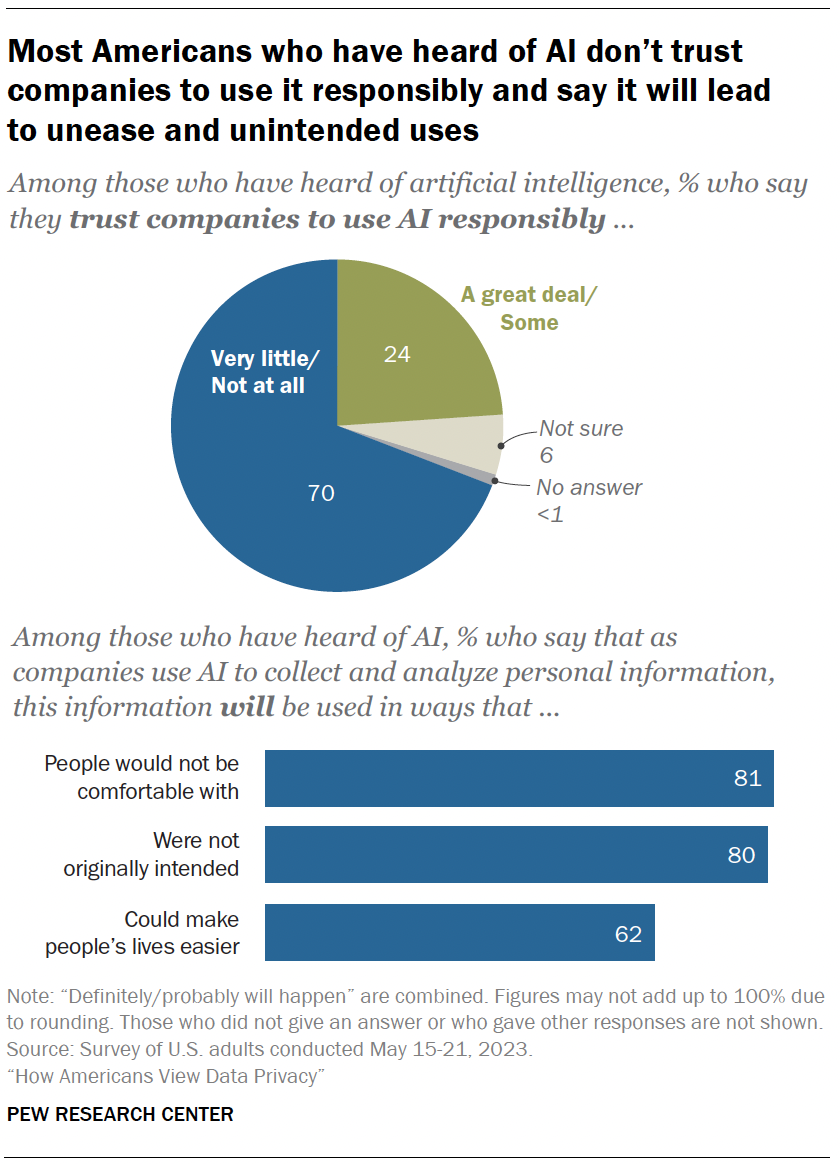
Trust in companies that use AI
In addition to understanding people’s comfort level with certain uses of AI, the survey also measured the public’s attitudes toward companies that are utilizing AI in their products.
Among those who have heard of AI:
- 70% say they have little to no trust in companies to make responsible decisions about how they use AI in their products.
- Roughly eight-in-ten say the information will be used in ways people are not comfortable with or that were not originally intended.
- Views are more mixed regarding the potential that using AI to analyze personal details could make life easier. A majority of those who have heard of AI say this will happen (62%). Regarding differences by age, adults under 50 are more optimistic than those 50 and older (70% vs. 54%).
Education differences
Among those who have heard of AI:
- 87% of those with a college degree or higher say companies will use AI to analyze personal details in ways people would not be comfortable with. Some 82% of those with some college experience and 74% with a high school diploma or less say the same.
- 88% of those with a bachelor’s degree or more say companies will use this information in ways that were not originally intended. This share drops to 80% among those with some college experience and 71% among those with a high school diploma or less.
- About three-quarters of those with a college degree or more (74%) say this information will be used in ways that could make people’s lives easier. But this share drops to 60% among those with some college experience and 52% among those with a high school diploma or less.
Types of Privacy Violations and Their Impact
Introduction:
In the world of cybersecurity, protecting personal and sensitive information is critical. Privacy violations, like cyberattacks, can have devastating effects on individuals and organizations. In this lesson, we will explore different types of privacy violations, their impact, and why they are so effective. We will also discuss Web3-specific privacy violations, as this emerging technology introduces unique challenges in protecting personal data.
1. Types of Privacy Violations
Data Breaches:
A data breach occurs when unauthorized individuals access personal data, often due to hacking, human error, or vulnerabilities in data storage. These breaches can expose sensitive information like Social Security numbers, credit card details, and health data.
- Impact: Identity theft, financial fraud, reputational damage, loss of consumer trust, and legal penalties for the organization responsible.
Surveillance:
Surveillance involves the unauthorized tracking of individuals through cameras, GPS, or online activities.
- Impact: Erosion of personal autonomy, anxiety, and fear of being watched. It may also violate civil liberties, leading to increased scrutiny or profiling.
Data Harvesting:
This occurs when organizations collect large amounts of personal information without proper consent, often for marketing or profit purposes. It can also involve collecting data through apps or websites that users unknowingly grant access to.
- Impact: Exploitation of personal data, unwanted advertising, and an increased risk of data breaches. It undermines privacy and often results in users feeling manipulated.
Phishing and Social Engineering:
Phishing involves tricking individuals into revealing sensitive information via fraudulent emails, phone calls, or text messages. Social engineering is a broader manipulation technique that exploits human error to gain unauthorized access to systems or data.
- Impact: Identity theft, financial loss, and a breach of personal privacy. These methods are effective because they exploit human trust and emotion, making individuals easy targets.
Inadequate Data Protection:
Failing to properly secure personal data can lead to privacy violations. This might involve weak passwords, lack of encryption, or failure to adhere to best practices in data storage.
- Impact: Increased risk of unauthorized access to personal data, financial loss, and regulatory penalties for the organization.
Sharing Data Without Consent:
This violation happens when an organization shares personal data with third parties without obtaining proper consent from the individual.
- Impact: Breach of trust, exposure to targeted marketing, and privacy violations. In many cases, individuals are unaware that their data is being shared.
Failure to Anonymize Data:
When personal data isn’t properly anonymized or de-identified, it can be exposed or re-identified, leading to privacy breaches.
- Impact: Loss of privacy, increased risk of exploitation, and potential misuse of sensitive information.
Misuse of Biometric Data:
Biometric data such as fingerprints, facial recognition, and voice patterns can be misused if not properly protected or stored.
- Impact: Identity theft, unlawful surveillance, and potential discrimination (e.g., biased facial recognition systems).
2. Web3-Specific Privacy Violations
Web3, which revolves around decentralized technologies like blockchain and smart contracts, introduces new opportunities and challenges related to privacy. While it promises enhanced security and transparency, it also brings about specific privacy concerns.
On-Chain Data Exposure:
In Web3, all transactions are recorded on a public blockchain. This means that while users may have pseudonymous identities, their transactions are visible to anyone who knows their address.
- Impact: While pseudonymous, transactions can be traced back to real-world identities through correlation with off-chain data, exposing users to risks like financial profiling, targeted attacks, and blackmail.
Wallet and Identity Leakage:
Web3 wallets are used for managing cryptocurrency and interacting with decentralized applications (dApps). However, if these wallets are not securely managed, the private keys or access credentials could be exposed, allowing attackers to access funds or personal information.
- Impact: Theft of assets, unauthorized access to Web3 platforms, and compromised user identity if linked to other personal data.
Lack of Data Minimization in Smart Contracts:
Smart contracts, which are self-executing contracts with the terms of the agreement directly written into code, may inadvertently expose sensitive data if they do not properly safeguard the privacy of participants.
- Impact: Unintended exposure of user data or transactional details, such as payment amounts, involved parties, and other sensitive information.
Decentralized Identity Theft:
In Web3, decentralized identity systems allow users to control their own identity without relying on centralized authorities. However, if these systems are not well-designed or secure, users' identities can be stolen or misused.
- Impact: Fraud, impersonation, and unauthorized access to sensitive decentralized services or assets. This also risks undermining the trust in decentralized identity systems.
Privacy Violations in DAO Governance:
Decentralized Autonomous Organizations (DAOs) rely on blockchain to manage governance decisions through smart contracts. If users' voting records or participation data are not properly protected, they may become subject to manipulation or public scrutiny.
- Impact: Loss of privacy in governance decisions, vulnerability to targeted attacks based on voting behavior, and compromise of personal data if linked to on-chain identities.
Phishing in Web3 (Crypto Phishing Scams):
Crypto phishing attacks target users in Web3 by posing as trusted Web3 services or platforms to steal private keys, seed phrases, or personal data.
- Impact: Theft of cryptocurrency, identity fraud, and loss of user assets. This type of attack exploits the lack of awareness of security risks in the Web3 space.
3. Why Privacy Violations Are Effective
Just like social engineering attacks in cybersecurity, privacy violations often exploit human psychology. Here’s why they work:
Trust Exploitation:
Individuals often trust organizations, websites, or services with their personal information. When this trust is violated, the effects can be damaging both emotionally and financially.
Lack of Awareness:
Many people are unaware of the risks associated with sharing personal information online or through other digital platforms. This ignorance makes them more susceptible to privacy violations.
The Appeal of Convenience:
People often prioritize convenience over security. For instance, apps that collect personal data are sometimes used without considering how that data might be exploited or mishandled.
Emotional Manipulation:
Similar to how threat actors manipulate victims in phishing attacks, privacy violations often involve emotional manipulation. For example, people might be pressured into sharing information due to fear of missing out, urgency, or authority figures making requests for their data.
4. Impact on Individuals and Organizations
For Individuals:
- Identity Theft: Personal information such as Social Security numbers, cryptocurrency wallet keys, and bank details can be stolen and used to impersonate the individual.
- Financial Loss: Unauthorized access to credit card information, cryptocurrencies, or bank accounts can lead to significant financial losses.
- Reputational Damage: If sensitive personal information is exposed, it can harm an individual’s reputation or social standing.
For Organizations:
- Legal Consequences: Organizations that fail to protect personal data or share it without consent may face hefty fines and legal repercussions, especially under laws like GDPR.
- Loss of Trust: Consumers are likely to abandon companies that fail to protect their privacy, leading to a loss of business and market share.
- Operational Disruption: Data breaches and privacy violations can lead to disruptions in business operations, particularly when data needs to be restored or when regulatory investigations occur.
Key Takeaways:
- Privacy violations can take many forms, from data breaches to misuse of biometric data. Each type carries significant consequences for both individuals and organizations.
- These violations are effective because they exploit trust, human psychology, and a lack of awareness regarding the risks involved in sharing personal data.
- Web3 introduces unique privacy challenges, such as on-chain data exposure and decentralized identity theft, requiring new approaches to safeguard user privacy in this evolving space.
- Understanding common privacy violations and their impact, especially in Web3, is crucial for protecting sensitive information and preventing harm to individuals and organizations.
Conclusion:
In this lesson, you learned about the different types of privacy violations and why they are so effective. By recognizing these violations and understanding their impacts, you can better safeguard personal information and take steps to protect yourself and others in the digital age, particularly as we navigate the emerging landscape of Web3 technologies.